[ad_1]
In the early morning of January 21, David Balland and his wife were forced at gunpoint into separate vehicles outside their home in Méreau, a commune in the opulent Loire Valley, France. The kidnappers had targeted Balland, who cofounded cryptocurrency wallet company Ledger, with the goal of winning a ransom, a prosecutor has claimed.
Build a website that pays you back with real revenue.
The kidnappers communicated their demands—the specifics of which have not been disclosed by law enforcement—to Éric Larchevêque, another Ledger cofounder. To flush out the full payment, they severed one of Balland’s fingers. French authorities dispatched more than two hundred officers to investigate.
On January 22, officers rescued Balland from a property in the neighbouring town of Châteauroux. They later discovered his wife—trussed up, but otherwise unharmed—in the back of a beaten up van.
These events were relayed by Paris prosecutor Laure Beccuau at a press conference on January 23, and in subsequent reports. The authorities had arrested ten people suspected to be connected to the kidnapping, Beccuau announced. For acts of “torture, barbarity and extortion,” she said, those arrested face up to life in prison if convicted.
Ledger declined to comment, citing the ongoing investigation and the need to afford privacy to Balland. In an X post Ledger CEO Pascal Gauthier said, “We are deeply relieved that David and his wife have been released.”
The grisly kidnapping—which came shortly after a crypto executive was held for ransom in Canada and the assassination of the United Healthcare CEO—has spooked the crypto industry. To protect themselves, wealthy crypto figures are turning to bodyguard services, which have experienced an influx of requests, sources with knowledge of the physical security sector tell WIRED.
“Like any human emotion, fear is a significant motivator…The headlines certainly mobilize a lot of that concern,” says Adam Healy, a former US Marine and chief executive at crypto-focused cybersecurity company Station 70, who frequently helps industry contacts to secure physical security services. “Demand has grown considerably.”
Because not every case of kidnap or extortion is reported, it is difficult to objectively assess the actual risk to wealthy figures in crypto. In making the fear of kidnap more acute, the headlines benefit the private security businesses, themselves incentivized to overstate the threat.
However, it is the case that people who control large amounts of crypto are more exposed to violent extortion than the typical executive by the nature of the technology: Unlike regular currency, crypto is stored in digital wallets protected only by alphanumeric keys. Because crypto transactions are irreversible, if a bad actor can coerce someone into handing over their key, they gain unfettered access to the coins in their wallet.
“That is one of the principles on which crypto was founded—the principle of self-custody. Not your keys, not your crypto,” says one crypto executive who has previously used bodyguard protection, who asked to remain anonymous for personal safety reasons. “It’s the equivalent to stuffing [your money in] your mattress.”
Over time, crypto organizations have taken steps to dilute the risk associated with self-custody, including by storing coins in special wallets that require the signature of multiple people for any transactions to take place. Sometimes, they go as far as to split wallet keys into several shards, each of which can be stored in a separate high-security bunker across the globe. But even elaborate measures only go so far in disincentivizing kidnap and attempted extortion.
[ad_2]
Source link
Related posts:
Stay Safe Online: Essential Tips for Safer Internet Day
Is Your Phone Your Best Friend or a Silent Spy?
Wipe Your Digital Footprints with Data Wipe Software
No, you’re not fired – but beware of job termination scams
DeceptiveDevelopment targets freelance developers
Fake job offers target coders with infostealers
Belarus-Linked Ghostwriter Uses Macropack-Obfuscated Excel Macros to Deploy Malware
LightSpy Expands to 100+ Commands, Increasing Control Over Windows, macOS, Linux, and Mobile
CISA Adds Microsoft and Zimbra Flaws to KEV Catalog Amid Active Exploitation
Malicious PyPI Package "automslc" Enables 104K+ Unauthorized Deezer Music Downloads
CERT-UA Warns of UAC-0173 Attacks Deploying DCRat to Compromise Ukrainian Notaries
Three Password Cracking Techniques and How to Defend Against Them
New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems
SOC 3.0 - The Evolution of the SOC and How AI is Empowering Human Talent
Leaked Black Basta Chat Logs Reveal $107M Ransom Earnings and Internal Power Struggles
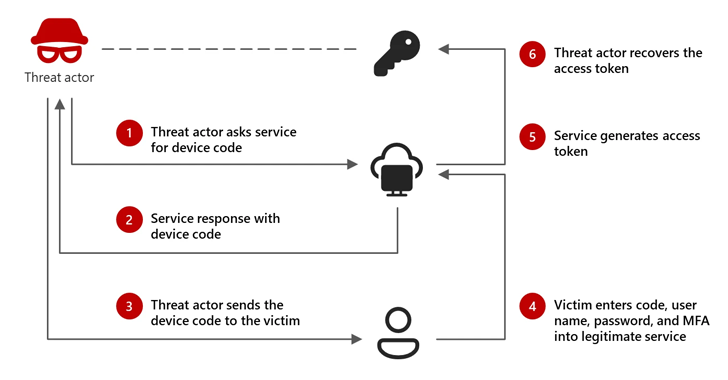
Microsoft: Russian-Linked Hackers Using 'Device Code Phishing' to Hijack Accounts
AI-Powered Social Engineering: Ancillary Tools and Techniques
Lazarus Group Deploys Marstech1 JavaScript Implant in Targeted Developer Attacks
New “whoAMI” Attack Exploits AWS AMI Name Confusion for Remote Code Execution
Android's New Feature Blocks Fraudsters from Sideloading Apps During Calls
New Golang-Based Backdoor Uses Telegram Bot API for Evasive C2 Operations
⚡ THN Weekly Recap: Google Secrets Stolen, Windows Hack, New Crypto Scams and More
CISO's Expert Guide To CTEM And Why It Matters
South Korea Suspends DeepSeek AI Downloads Over Privacy Violations
Microsoft Uncovers New XCSSET macOS Malware Variant with Advanced Obfuscation Tactics
Cybercriminals Exploit Onerror Event in Image Tags to Deploy Payment Skimmers
New Xerox Printer Flaws Could Let Attackers Capture Windows Active Directory Credentials
Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign
Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication
Debunking the AI Hype: Inside Real Hacker Tactics
Build a website that pays you back with real revenue.