[ad_1]
The difference between a conventional model and a reasoning one is similar to the two types of thinking described by the Nobel-prize-winning economist Michael Kahneman in his 2011 book Thinking Fast and Slow: fast and instinctive System-1 thinking and slower more deliberative System-2 thinking.
Build a website that pays you back with real revenue.
The kind of model that made ChatGPT possible, known as a large language model or LLM, produces instantaneous responses to a prompt by querying a large neural network. These outputs can be strikingly clever and coherent but may fail to answer questions that require step-by-step reasoning, including simple arithmetic.
An LLM can be forced to mimic deliberative reasoning if it is instructed to come up with a plan that it must then follow. This trick is not always reliable, however, and models typically struggle to solve problems that require extensive, careful planning. OpenAI, Google, and now Anthropic are all using a machine learning method known as reinforcement learning to get their latest models to learn to generate reasoning that points toward correct answers. This requires gathering additional training data from humans on solving specific problems.
Penn says that Claude’s reasoning mode received additional data on business applications including writing and fixing code, using computers, and answering complex legal questions. “The things that we made improvements on are … technical subjects or subjects which require long reasoning,” Penn says. “What we have from our customers is a lot of interest in deploying our models into their actual workloads.”
Anthropic says that Claude 3.7 is especially good at solving coding problems that require step-by-step reasoning, outscoring OpenAI’s o1 on some benchmarks like SWE-bench. The company is today releasing a new tool, called Claude Code, specifically designed for this kind of AI-assisted coding.
“The model is already good at coding,” Penn says. But “additional thinking would be good for cases that might require very complex planning—say you’re looking at an extremely large code base for a company.”
[ad_2]
Source link
Related posts:
Stay Safe Online: Essential Tips for Safer Internet Day
Is Your Phone Your Best Friend or a Silent Spy?
Wipe Your Digital Footprints with Data Wipe Software
No, you’re not fired – but beware of job termination scams
DeceptiveDevelopment targets freelance developers
Fake job offers target coders with infostealers
Belarus-Linked Ghostwriter Uses Macropack-Obfuscated Excel Macros to Deploy Malware
LightSpy Expands to 100+ Commands, Increasing Control Over Windows, macOS, Linux, and Mobile
CISA Adds Microsoft and Zimbra Flaws to KEV Catalog Amid Active Exploitation
Malicious PyPI Package "automslc" Enables 104K+ Unauthorized Deezer Music Downloads
CERT-UA Warns of UAC-0173 Attacks Deploying DCRat to Compromise Ukrainian Notaries
Three Password Cracking Techniques and How to Defend Against Them
New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems
SOC 3.0 - The Evolution of the SOC and How AI is Empowering Human Talent
Leaked Black Basta Chat Logs Reveal $107M Ransom Earnings and Internal Power Struggles
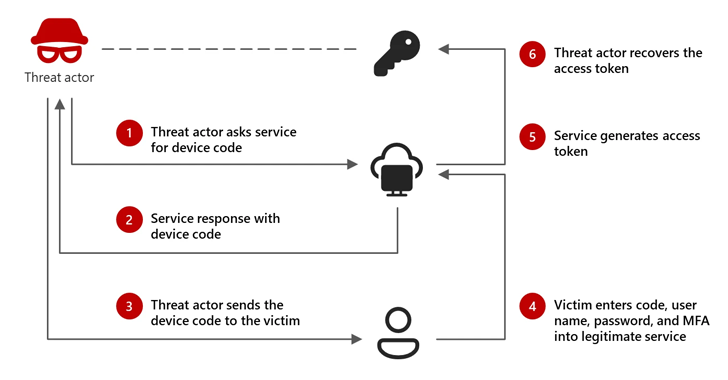
Microsoft: Russian-Linked Hackers Using 'Device Code Phishing' to Hijack Accounts
AI-Powered Social Engineering: Ancillary Tools and Techniques
Lazarus Group Deploys Marstech1 JavaScript Implant in Targeted Developer Attacks
New “whoAMI” Attack Exploits AWS AMI Name Confusion for Remote Code Execution
Android's New Feature Blocks Fraudsters from Sideloading Apps During Calls
New Golang-Based Backdoor Uses Telegram Bot API for Evasive C2 Operations
⚡ THN Weekly Recap: Google Secrets Stolen, Windows Hack, New Crypto Scams and More
CISO's Expert Guide To CTEM And Why It Matters
South Korea Suspends DeepSeek AI Downloads Over Privacy Violations
Microsoft Uncovers New XCSSET macOS Malware Variant with Advanced Obfuscation Tactics
Cybercriminals Exploit Onerror Event in Image Tags to Deploy Payment Skimmers
New Xerox Printer Flaws Could Let Attackers Capture Windows Active Directory Credentials
Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign
Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication
Debunking the AI Hype: Inside Real Hacker Tactics
Build a website that pays you back with real revenue.