[ad_1]
Over the weekend, Elon Musk surveyed his followers on X — the platform he spent $44 billion to buy — asking whether federal employees should be required to send his team an email with a list of five things they accomplished this week. With the yes votes totaling over 70%, Musk followed through. Federal employees received an email from the U.S. Office of Personnel Management (OPM) this weekend, requesting their weekly list of accomplishments by 11:59 p.m. ET on Monday.
Build a website that pays you back with real revenue.
“Consistent with [President Donald Trump’s] instructions, all federal employees will shortly receive an email requesting to understand what they got done last week,” Musk wrote on X. “Failure to respond will be taken as a resignation.”
With millions of employees across the federal government, the DOGE-operated email address and the contents of the email were bound to leak. As federal employees are threatened with losing their jobs, people on social media platforms like Reddit, TikTok, Threads, and Bluesky are calling on each other to spam the now-public email address with nonsense.
This is a common tactic of online resistance when something like a controversial form for public comment or email address gets out.
In one case, so many people sent the complete script of the “Bee Movie” — a recurring internet joke — to an anti-trans “snitch form” in Missouri that the tip line was taken offline. People responded similarly to a Texas state inbox tracking gender marker changes on driver’s licenses, as well as an anti-trans bathroom complaint form in Utah.
This online vigilantism sometimes coalesces within particular communities, like the K-pop fandom. In 2020, Dallas police requested that people send them videos of illegal activity taking place during protests following the police killing of George Floyd; instead, fans of Korean superstars like BTS spammed the police department’s app with nonsensical fancam videos.
Trump’s detractors have employed these tactics since the first week of his term, when his administration set up dedicated email accounts requesting that employees report noncompliance with the president’s executive orders to dismantle diversity, equity, and inclusion (DEI) programs. Workers were threatened with imprecise “adverse consequences” if they withheld information about efforts to “obscure the connection” between DEI initiatives and government contracts.
Though OPM is a long-standing government agency, these specific email addresses are new. Federal employees first received an email from the OPM’s HR email address in January, testing whether it could be used to contact all government workers in one email blast. This move sparked a class-action lawsuit from two whistleblowers who claim it violates federal privacy law to create this brand-new email server without following established security measures.
These security protocols are in place for a reason. In 2015, the OPM was hacked, compromising sensitive data from security clearance background checks for 21.5 million people. That included the Social Security numbers of each of these individuals, as well as biometric data from 1.1 million people. Musk’s DOGE team, meanwhile, has been granted unprecedented power and broad access to these government systems with little resistance.
It’s unclear how effectively DOGE will be deterred by this mass spam campaign. Since ordinary people do not have .gov email addresses, it’s possible that Musk’s team could just filter their inboxes for government-only email addresses. The inbox could also collapse under the sheer volume of mail it will receive; if Musk’s DOGE team is using a physical server, then the amount of data it can contain is finite.
Though it’s possible these efforts could be futile, people who resist Musk’s policies are not deterred — after all, it doesn’t take very long to copy and paste the complete script of the “Bee Movie” into an email.
[ad_2]
Source link
Related posts:
Stay Safe Online: Essential Tips for Safer Internet Day
Is Your Phone Your Best Friend or a Silent Spy?
Wipe Your Digital Footprints with Data Wipe Software
No, you’re not fired – but beware of job termination scams
DeceptiveDevelopment targets freelance developers
Fake job offers target coders with infostealers
Belarus-Linked Ghostwriter Uses Macropack-Obfuscated Excel Macros to Deploy Malware
LightSpy Expands to 100+ Commands, Increasing Control Over Windows, macOS, Linux, and Mobile
CISA Adds Microsoft and Zimbra Flaws to KEV Catalog Amid Active Exploitation
Malicious PyPI Package "automslc" Enables 104K+ Unauthorized Deezer Music Downloads
CERT-UA Warns of UAC-0173 Attacks Deploying DCRat to Compromise Ukrainian Notaries
Three Password Cracking Techniques and How to Defend Against Them
New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems
SOC 3.0 - The Evolution of the SOC and How AI is Empowering Human Talent
Leaked Black Basta Chat Logs Reveal $107M Ransom Earnings and Internal Power Struggles
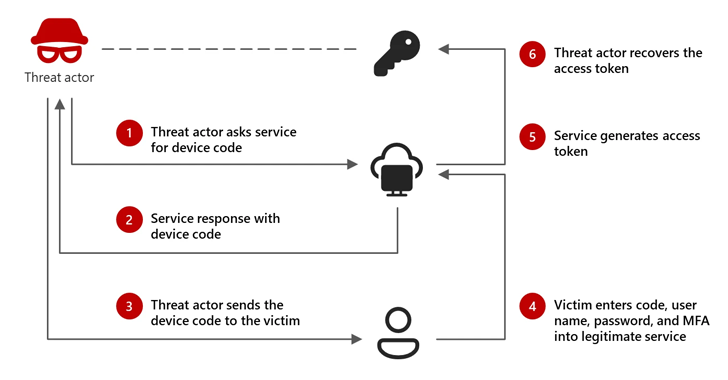
Microsoft: Russian-Linked Hackers Using 'Device Code Phishing' to Hijack Accounts
AI-Powered Social Engineering: Ancillary Tools and Techniques
Lazarus Group Deploys Marstech1 JavaScript Implant in Targeted Developer Attacks
New “whoAMI” Attack Exploits AWS AMI Name Confusion for Remote Code Execution
Android's New Feature Blocks Fraudsters from Sideloading Apps During Calls
New Golang-Based Backdoor Uses Telegram Bot API for Evasive C2 Operations
⚡ THN Weekly Recap: Google Secrets Stolen, Windows Hack, New Crypto Scams and More
CISO's Expert Guide To CTEM And Why It Matters
South Korea Suspends DeepSeek AI Downloads Over Privacy Violations
Microsoft Uncovers New XCSSET macOS Malware Variant with Advanced Obfuscation Tactics
Cybercriminals Exploit Onerror Event in Image Tags to Deploy Payment Skimmers
New Xerox Printer Flaws Could Let Attackers Capture Windows Active Directory Credentials
Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign
Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication
Debunking the AI Hype: Inside Real Hacker Tactics
Build a website that pays you back with real revenue.