[ad_1]
“Regrettably, I found no available source online to know more about this organization except for those registrations,” wrote the complainant. “They are collecting huge amounts of investment from third world countries in Asia.”
Build a website that pays you back with real revenue.
One of the FTC complaints alleges that over 6,000 people in Bangladesh were potentially impacted by the OpenAi-etc job scam. The ages listed in the FTC complaints range from teenagers to people in their fifties, with locations spread across multiple Bangladesh cities, from Dhaka to Khulna.
“My next trading date was 29 August, 2024,” wrote another complainant. “I made the trade with my whole amount in the evening. But, suddenly, the OpenAI company vanished. I didn’t withdraw any money but lost both capital and profit. Now, I am in a great economic crisis, as I am a normal school teacher.”
Niko Felix, a spokesperson for OpenAI, declined to answer questions about whether the startup was previously aware of the “OpenAi-etc” scam, or if they planned to take action against the fraudsters. But he did share that OpenAI is investigating the matter. The alleged scam website is no longer available online, and WIRED was not able to contact the people behind “OpenAi-etc” prior to publication.
A Telegram spokesperson using the name Remi Vaughn tells WIRED that the company monitors its platform for scams, such as those allegedly carried out by OpenAi-etc, which used the messaging app to communicate with people who believed they were working for the company.
“Telegram actively moderates harmful content on its platform, including scams,” Vaughn says in a statement sent to WIRED through the messaging platform. “Moderators empowered with custom Al and machine learning tools proactively monitor public parts of the platform and accept reports from users and organizations in order to remove millions of pieces of harmful content each day.”
The usual pattern of a crypto job scam is to trick people into depositing some kind of digital currency into a fake account the victim believes they have control over, until the perpetrator drains it one day without warning. While this specific rug pull used OpenAI’s branding to allegedly dupe its victims, a crypto job scam can happen with the name of any company that has enough widespread recognition for criminals to capitalize on.
“These social engineering scams are designed to lower our natural suspicion and to make us complicit in our own deception,” says Arun Vishwanath, a cybersecurity expert and author of The Weakest Link. “For job scams, they try to turn our ambitions and inherent trust in brands into a vulnerability.” Similar to so-called pig butchering investment scams, a key component often includes direct messages over a long period of time to cultivate a sense of trust with the targets.
Although comparable job scams happen all over the world, Vishwanath believes that Asian cultural norms of so-called high power distance, where there’s more acceptance of interpersonal hierarchies, are a contributing factor. “Authorities are expected to ask you things and make you do things,” he says. “And you just comply.” Scammers are taking advantage of this by imitating authority figures and leaning into the sense of urgency inherent to searching for a job.
Bangladeshi citizens on the difficult hunt for reliable work have increasingly been targeted by job scammers in recent years. Lies about international job opportunities have left throngs of would-be workers stranded in Malaysia, and at least three cases of kidney organ theft were reported by people lured to India with false promises of work.
[ad_2]
Source link
Related posts:
Stay Safe Online: Essential Tips for Safer Internet Day
Is Your Phone Your Best Friend or a Silent Spy?
Wipe Your Digital Footprints with Data Wipe Software
No, you’re not fired – but beware of job termination scams
DeceptiveDevelopment targets freelance developers
Fake job offers target coders with infostealers
Belarus-Linked Ghostwriter Uses Macropack-Obfuscated Excel Macros to Deploy Malware
LightSpy Expands to 100+ Commands, Increasing Control Over Windows, macOS, Linux, and Mobile
CISA Adds Microsoft and Zimbra Flaws to KEV Catalog Amid Active Exploitation
Malicious PyPI Package "automslc" Enables 104K+ Unauthorized Deezer Music Downloads
CERT-UA Warns of UAC-0173 Attacks Deploying DCRat to Compromise Ukrainian Notaries
Three Password Cracking Techniques and How to Defend Against Them
New Linux Malware ‘Auto-Color’ Grants Hackers Full Remote Access to Compromised Systems
SOC 3.0 - The Evolution of the SOC and How AI is Empowering Human Talent
Leaked Black Basta Chat Logs Reveal $107M Ransom Earnings and Internal Power Struggles
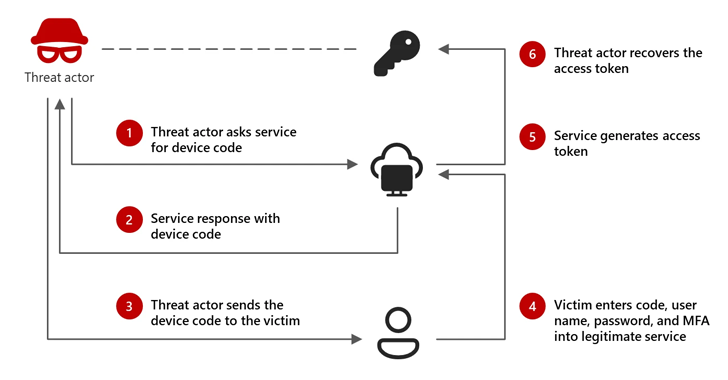
Microsoft: Russian-Linked Hackers Using 'Device Code Phishing' to Hijack Accounts
AI-Powered Social Engineering: Ancillary Tools and Techniques
Lazarus Group Deploys Marstech1 JavaScript Implant in Targeted Developer Attacks
New “whoAMI” Attack Exploits AWS AMI Name Confusion for Remote Code Execution
Android's New Feature Blocks Fraudsters from Sideloading Apps During Calls
New Golang-Based Backdoor Uses Telegram Bot API for Evasive C2 Operations
⚡ THN Weekly Recap: Google Secrets Stolen, Windows Hack, New Crypto Scams and More
CISO's Expert Guide To CTEM And Why It Matters
South Korea Suspends DeepSeek AI Downloads Over Privacy Violations
Microsoft Uncovers New XCSSET macOS Malware Variant with Advanced Obfuscation Tactics
Cybercriminals Exploit Onerror Event in Image Tags to Deploy Payment Skimmers
New Xerox Printer Flaws Could Let Attackers Capture Windows Active Directory Credentials
Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign
Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication
Debunking the AI Hype: Inside Real Hacker Tactics
Build a website that pays you back with real revenue.